13 Feb 2018

In the last 24 hours, it has been discovered that a vulnerability in the Browsealoud plugin allowed hackers to hijack the machines of users visiting affected sites, in order to mine crypto-currency.
The exploit hit all domains that host Browsealoud, including sites run by the NHS, the Australian government, universities and the US government’s court system. The plugin normally reads web text for people who are blind or who suffer from vision impairment. However, after being compromised, it invisibly directed users to run the Monero crypto-currency mining software. From the perspective of users, the code should be stopped by most antivirus packages and it does not persist after the tab is closed – however, an exploit of this nature could be used for a wide variety of much more nefarious purposes such as keystroke logging, stealing passwords or transmitting malware.
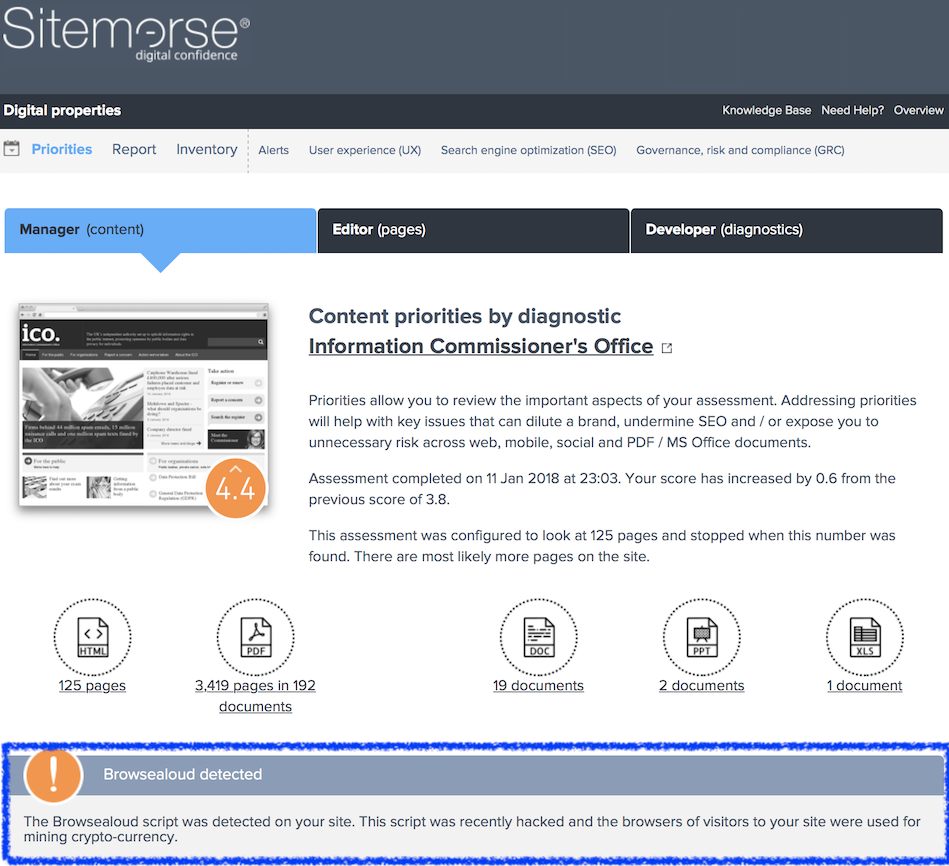
Of course, for digital teams, the breach highlights the importance of knowing exactly what you have on your page and why. If you don’t, then you’re not even able to assess the level of risk that you may be exposed to, let alone in a position to tackle the issue or to promptly resolve it. It’s important to have automation in places to scan pages quickly and to pinpoint any potential problems and precisely where they’re occurring – and the Browsealoud breach is just one example of what can go wrong if you don’t have that resource in place.
Effective digital governance isn’t about hoping – it’s about monitoring, managing and updating. Only then can you have confidence. That’s exactly why rather than supply endless reporting, we focus on providing our clients with concise lists of actionable recommendations that allow digital teams to make big changes, fast.
The Browsealoud service was taken offline by the provider, Texthelp, on Sunday 11th February and is expected to come back online on Tuesday 13th February. Nevertheless, some digital managers are removing the code in the meantime with the view that the benefits of having the Browsealoud JavaScript running on their site are outweighed by the risks. More comprehensive strategies to block hacks like these are possible, but they are also very complex.
Further ideas, thoughts on Content Security Policies that would have helped a lot in this situation https://www.troyhunt.com/the-javascript-supply-chain-paradox-sri-csp-and-trust-in-third-party-libraries/
The press release from the company here: https://www.texthelp.com/en-gb/company/corporate-blog/february-2018/data-security-investigation-underway-at-texthelp/
If you have any questions about the Browsealoud breach or would like to check if you are affected, please contact us at info@sitemorse.com

